We now house the first engineering and data science team focused solely on developing new technologies to combat online child sexual abuse. We bring together a team with deep technical knowledge and subject matter expertise to innovate and deploy new technology solutions at a much faster rate. We are able to quickly assess whether new technologies can be repurposed to protect children from sexual exploitation through one of our three strategic pillars: 1) accelerating victim identification 2) equipping platforms, and 3) empowering the public.
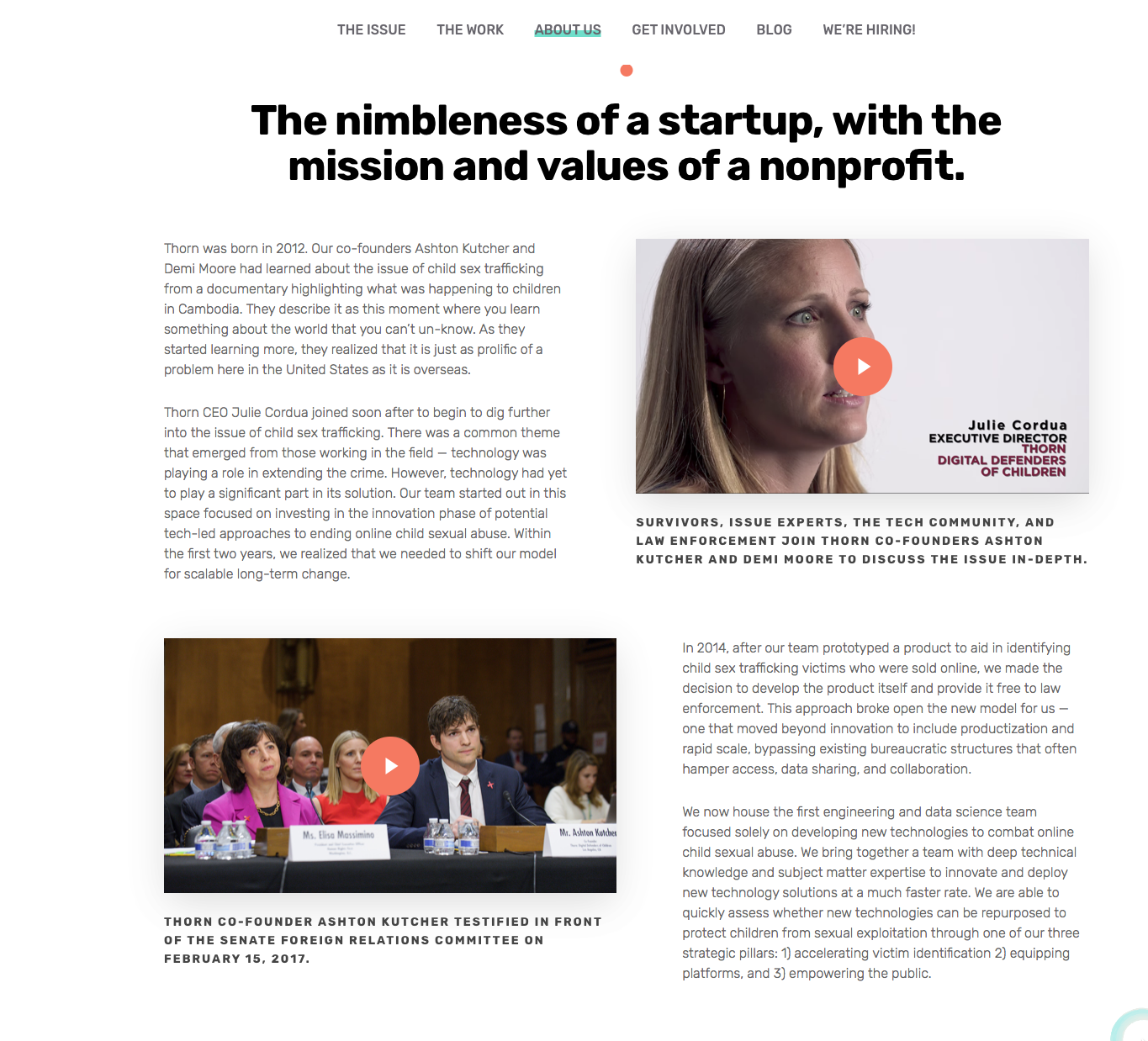
Thorn was born in 2012. Our co-founders Ashton Kutcher and Demi Moore had learned about the issue of child sex trafficking from a documentary highlighting what was happening to children in Cambodia. They describe it as this moment where you learn something about the world that you can’t un-know. As they started learning more, they realized that it is just as prolific of a problem here in the United States as it is overseas.
Thorn CEO Julie Cordua joined soon after to begin to dig further into the issue of child sex trafficking. There was a common theme that emerged from those working in the field — technology was playing a role in extending the crime. However, technology had yet to play a significant part in its solution. Our team started out in this space focused on investing in the innovation phase of potential tech-led approaches to ending online child sexual abuse. Within the first two years, we realized that we needed to shift our model for scalable long-term change.
In 2014, after our team prototyped a product to aid in identifying child sex trafficking victims who were sold online, we made the decision to develop the product itself and provide it free to law enforcement. This approach broke open the new model for us — one that moved beyond innovation to include productization and rapid scale, bypassing existing bureaucratic structures that often hamper access, data sharing, and collaboration.